In April of this year an online group called The Shadow Brokers released a treasure trove of documents and tools stolen from the US security agency NSA who used these tools to hack and spy on computers all over the world. Among them was a tool codenamed Eternalblue. EternalBlue used a previously unknown vulnerability in Windows computers to make its way into an unsuspecting network of computers.
The security leak by the NSA made all these tools available to the public to use in any they wanted. Someone, we don’t yet know who, weaponized this tool and turned it into a ransomware software. What ‘ransomware’ basically does is hold a metaphorical gun to your computer’s head, allowing hackers to hold your computer hostage until you pay them. If you refuse, you lose all your data and your files.
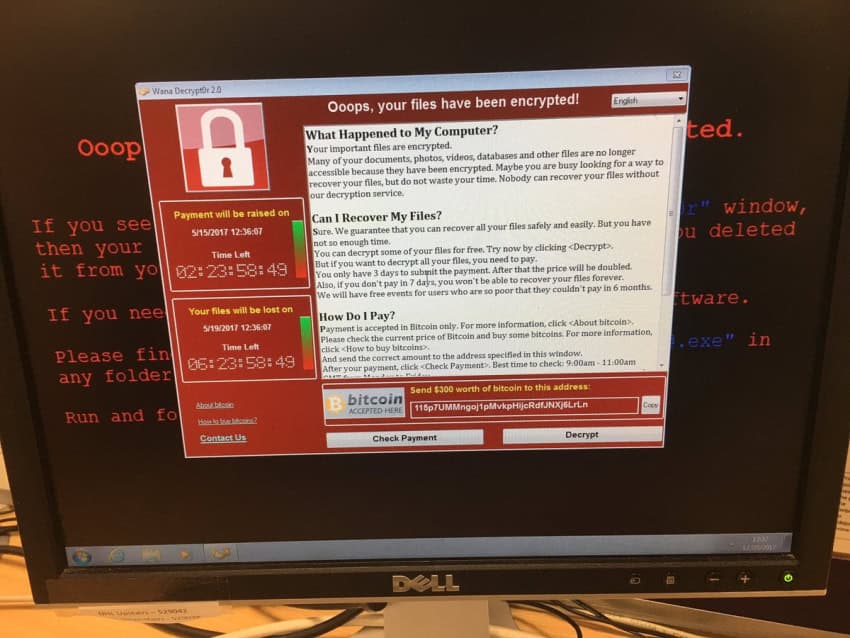
The result was WanaCrypt0r 2.0, or WannaCrypt. This tool travels from computer to computer on a network hidden in Word Documents and PDFs. Once it installs itself on the host computer it encrypts all the files on that system, making them unsuable. Then it displays a message telling the user what it has done and demands $300 to free the now hostage computer.
Related: Hospital computers across England shut down by cyberattack, reports of hackers demanding ransom
WannaCrypt attacked computers in Britain’s NHS yesterday and from NHS’ internal network it spread all over the world. Its victims include hospitals and some of the world’s largest companies, including the Telecom giant Telefonica in Spain. This prompted Microsoft to release urgent security patches and taking the unprecedented step of releasing a security patch for Windows XP, an operating system that Microsoft has stopped supporting.
But then suddenly, on the morning of 13th May (PST), the virus stopped spreading. This was because of one man and his dicovery of a magic kill-switch inside the tool.
Twitter user MalwareTech, a security analyst, dicovered a line of code inside the tool. That line checked for a domain, a URL on the internet, before spreading itself. The tool checked for the existence of a domain, and if it existed, it would not spread itself. But if the domain didn’t exist, it would keep spreading – but malwareTech didn’t know that part. That domain was “iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com”. Since no one had registered or owned the domain before, MalwareTech decided to register that domain on a hunch. As soon as MalwareTech registered that domain, the virus stopped spreading – as if by magic.
https://twitter.com/MalwareTechBlog/status/863187104716685312
https://twitter.com/MalwareTechBlog/status/863189077843116032
The threat still exists
MalwareTech’s actions have temporarily stopped the spread of this virus and there is a strong chance that it will return, better and stronger.
Microsoft has released patches for WannaCrypt for all versions of its Windows Operating System. If you have Automatic Updates enabled on your computer, you are already patched. You can also download these patches from the windows website, as instructed in their security bulletin.
If you run Windows XP, you should immediately upgrade because Windows has stopped supporting this operating system. Even though Microsoft released a patch for WannaCrypt this time, there is no guarantee that Microsoft will do so for similar attacks in the future.
WannaCrypt in Pakistan
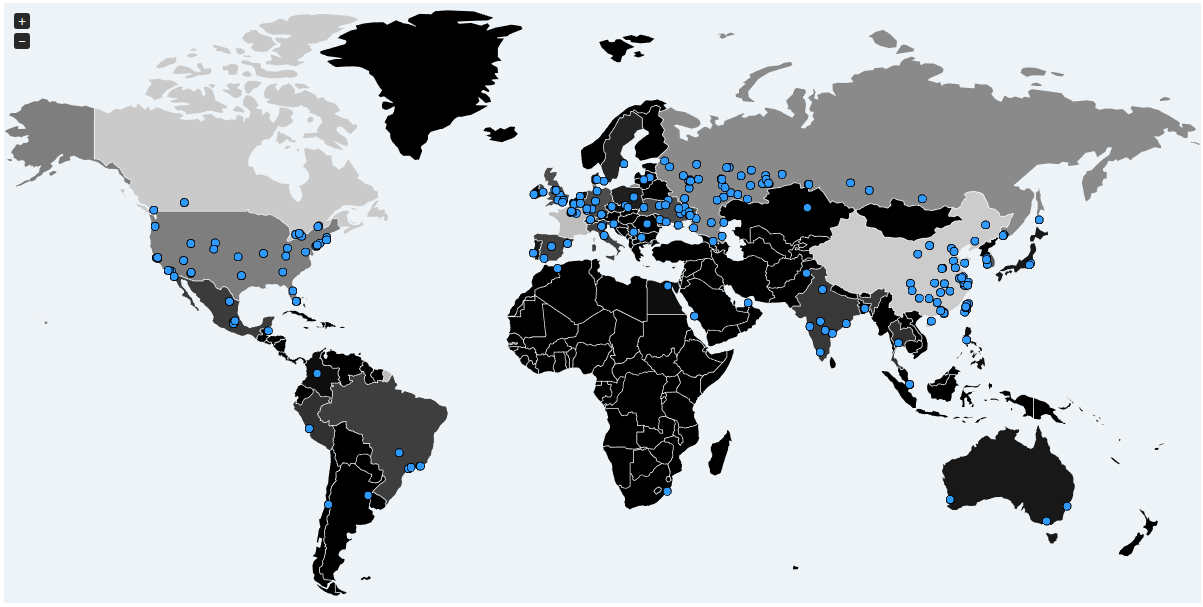
According to the map and data provided by MalwareTech, WannaCrypt has already hit Pakistani computers, particularly in Islamabad. However, it was stopped by our hero, MalwareTech before it did large-scale damage in Pakistan. This may prove temporary, therefore all Pakistani Windows users are advised to apply the security patches provided by Microsoft.
There are many universities, schools, hospitals and government offices that still use Windows XP. Windows XP is an insecure and unsupported system. Older systems can either be switched to Linux, which is a far more secure operating system, or to newer versions of Microsoft Windows, if the hardware is supported.